About Apollo Hospitals:-
In 2015, Apollo Hospitals introduced its digital platform, Ask Apollo. The platform provides remote healthcare services. The platform connects patients with doctors remotely and provides services like a consultation with doctors via video, voice calls, and email. Apollo developed the platform in partnership with the Hyderabad-based emergency and healthcare management services firm, HealthNet Global and Vidyo
source: Wikipedia
I stumbled on this bug while I was booking a dental appointment with Apollo hospitals. This bug was leaking 1 MILLION customers details who booked an appoint online with apollo hospitals.
Since they are a big company, I thought it was my moral responsibility to help them get it fixed. But unfortunately, they never replied to my emails.
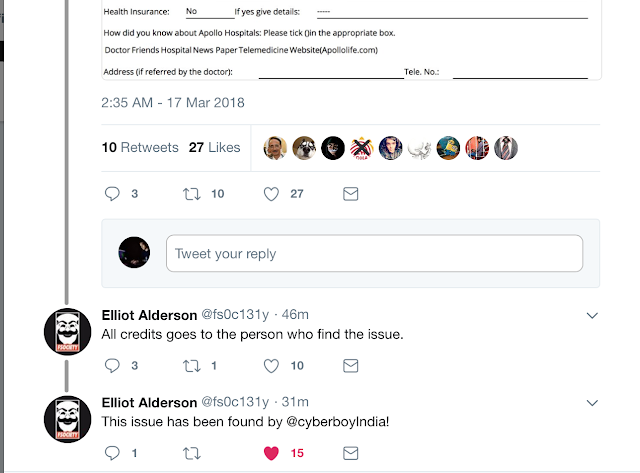
Then one day I heard of a nice guy named Elliot. Who disclosed a lot of vulnerabilities in Indian companies privately and helped them get it patched. So, I asked him if he could contact because he had more chances of getting a response.
And that worked. I am glad that apollo patched the vulnerability. But I wish like other companies they had a responsible disclosure program through which anyone could help them patch security issues in an ethical manner.
Details of the security issue:-
So Apollo Hospitals has an online appointment booking portal "www.askapollo.com" .
When we sign up, we get our profile created.
Now there is an option to print IPR form. When I clicked on it. I got my IPR form auto-filled.
The autofill request bought me into suspicion hence. I tried to look whats was going on in the background.
So the URL was
"https://www.askapollo.com/physical-appointment/PrintIPRForm.aspx?hashKey=11534XX"
Unfortunately hash key was not at all a hash, it was a plain sequential number. I tried to reduce the sequential ID. VIOLA an IDOR, I could see other persons IPA form which had sensitive informations like
Name
Address
DOB
Phone number
Email etc.
My sequential id was 11534XX which is (7 digits)... So, around 1 MILLION details of users could possibly get leaked if went in wrong hands.
I would like to thank Elliot again for creating awareness among Indian companies about the importance of security when everything is getting online.
Final words
We talk about Digital India but we are lacking very basic security measures almost everywhere. And as we are going more and more digital it's very essential that companies should handle their customer's data in a secure manner and one of the best methods is to have a responsible disclosure program.
A responsible disclosure policy is the initial first step in helping protect your company from an attack or premature vulnerability release to the public. The best part is they aren’t hard to set up and provide your team peace of mind when a researcher discovers a vulnerability. Getting started with responsible disclosure simply requires a security page that states –
What parts or sections of a site are within testing scope.
The types of bugs and vulns that are valid for submission.
A dedicated security email address to report the issue (often [email protected]).
https://www.bugcrowd.com/resource/what-is-responsible-disclosure/ (For more details)
If we look into counties like the USA... Their airforce, pentagon, defense websites, etc. have also adopted responsible disclosure program. These actions and understanding make the USA ahead of India.
Example is here
https://hackerone.com/htaf2
If we look at facts and figures. Indians received the highest amount of rewards from facebook.com's bug-bounty program. Facebook rewards ethical hackers for finding and reporting security vulnerabilities on Facebook's website. This means we do have resources but we are neglecting it.
~Source
https://www.facebook.com/notes/facebook-bug-bounty/facebook-bug-bounty-5-million-paid-in-5-years/1419385021409053/
Another source
https://economictimes.indiatimes.com/tech/internet/bsnl-isro-cases-show-india-not-a-country-for-ethical-hackers/articleshow/63278882.cms?from=mdr
Indian companies need to be more open towards ethical hackers rather than being orthodox. Blogging about this bug was not to shame anyone. Its to spread awareness that we have to take security seriously, which is highly neglected in India.
Let's make the Internet a safer place :)
In 2015, Apollo Hospitals introduced its digital platform, Ask Apollo. The platform provides remote healthcare services. The platform connects patients with doctors remotely and provides services like a consultation with doctors via video, voice calls, and email. Apollo developed the platform in partnership with the Hyderabad-based emergency and healthcare management services firm, HealthNet Global and Vidyo
source: Wikipedia
I stumbled on this bug while I was booking a dental appointment with Apollo hospitals. This bug was leaking 1 MILLION customers details who booked an appoint online with apollo hospitals.
Since they are a big company, I thought it was my moral responsibility to help them get it fixed. But unfortunately, they never replied to my emails.
Then one day I heard of a nice guy named Elliot. Who disclosed a lot of vulnerabilities in Indian companies privately and helped them get it patched. So, I asked him if he could contact because he had more chances of getting a response.
And that worked. I am glad that apollo patched the vulnerability. But I wish like other companies they had a responsible disclosure program through which anyone could help them patch security issues in an ethical manner.
Details of the security issue:-
So Apollo Hospitals has an online appointment booking portal "www.askapollo.com" .
When we sign up, we get our profile created.
The autofill request bought me into suspicion hence. I tried to look whats was going on in the background.
"https://www.askapollo.com/physical-appointment/PrintIPRForm.aspx?hashKey=11534XX"
Unfortunately hash key was not at all a hash, it was a plain sequential number. I tried to reduce the sequential ID. VIOLA an IDOR, I could see other persons IPA form which had sensitive informations like
Name
Address
DOB
Phone number
Email etc.
My sequential id was 11534XX which is (7 digits)... So, around 1 MILLION details of users could possibly get leaked if went in wrong hands.
I would like to thank Elliot again for creating awareness among Indian companies about the importance of security when everything is getting online.
Final words
We talk about Digital India but we are lacking very basic security measures almost everywhere. And as we are going more and more digital it's very essential that companies should handle their customer's data in a secure manner and one of the best methods is to have a responsible disclosure program.
A responsible disclosure policy is the initial first step in helping protect your company from an attack or premature vulnerability release to the public. The best part is they aren’t hard to set up and provide your team peace of mind when a researcher discovers a vulnerability. Getting started with responsible disclosure simply requires a security page that states –
What parts or sections of a site are within testing scope.
The types of bugs and vulns that are valid for submission.
A dedicated security email address to report the issue (often [email protected]).
https://www.bugcrowd.com/resource/what-is-responsible-disclosure/ (For more details)
If we look into counties like the USA... Their airforce, pentagon, defense websites, etc. have also adopted responsible disclosure program. These actions and understanding make the USA ahead of India.
Example is here
https://hackerone.com/htaf2
If we look at facts and figures. Indians received the highest amount of rewards from facebook.com's bug-bounty program. Facebook rewards ethical hackers for finding and reporting security vulnerabilities on Facebook's website. This means we do have resources but we are neglecting it.
~Source
https://www.facebook.com/notes/facebook-bug-bounty/facebook-bug-bounty-5-million-paid-in-5-years/1419385021409053/
Another source
https://economictimes.indiatimes.com/tech/internet/bsnl-isro-cases-show-india-not-a-country-for-ethical-hackers/articleshow/63278882.cms?from=mdr
Indian companies need to be more open towards ethical hackers rather than being orthodox. Blogging about this bug was not to shame anyone. Its to spread awareness that we have to take security seriously, which is highly neglected in India.
Let's make the Internet a safer place :)